​what Type Of Access Control List Defines The Settings For Auditing Access To An Object?
What is an access control list (ACL)?
An access control list (ACL) is a list of rules that specifies which users or systems are granted or denied access to a particular object or system resources. Access command lists are besides installed in routers or switches, where they deed as filters, managing which traffic can access the network.
Each system resource has a security attribute that identifies its access control list. The list includes an entry for every user who tin access the system. The near mutual privileges for a file system ACL include the power to read a file or all the files in a directory, to write to the file or files, and to execute the file if it is an executable file or program. ACLs are too built into network interfaces and operating systems (OSes), including Linux and Windows. On a computer network, admission control lists are used to prohibit or allow certain types of traffic to the network. They commonly filter traffic based on its source and destination.
What are access control lists used for?
Access control lists are used for decision-making permissions to a reckoner system or figurer network. They are used to filter traffic in and out of a specific device. Those devices can be network devices that human activity as network gateways or endpoint devices that users access direct.
On a reckoner system, certain users have different levels of privilege, depending on their role. For example, a user logged in as network administrator may have read, write and edit permissions for a sensitive file or other resources. By contrast, a user logged in as a guest may only have read permissions.
Access command lists can help organize traffic to improve network efficiency and to give network administrators granular control over users on their calculator systems and networks. ACLs tin also be used to improve network security by keeping out malicious traffic.
How do ACLs work?
Each ACL has one or more than access control entries (ACEs) consisting of the name of a user or group of users. The user can also be a part proper name, such as programmer or tester. For each of these users, groups or roles, the admission privileges are stated in a string of $.25 called an admission mask. Generally, the arrangement administrator or the object owner creates the access control list for an object.
Types of access control lists
At that place are two basic types of ACLs:
- File organization ACLs manage access to files and directories. They give OSes the instructions that constitute user access permissions for the system and their privileges once the system has been accessed.
- Networking ACLs manage network access past providing instructions to network switches and routers that specify the types of traffic that are immune to interface with the network. These ACLs also specify user permissions once inside the network. The network ambassador predefines the networking ACL rules. In this way, they part similar to a firewall.
ACLs can also be categorized by the way they identify traffic:
- Standard ACLs block or allow an entire protocol suite using source IP addresses.
- Extended ACLs block or permit network traffic based on a more than differentiated ready of characteristics that includes source and destination IP addresses and port numbers, as opposed to just source address.
Benefits of using an ACL
At that place are several benefits of using an ACL, including the following:
- Simplified user identification. An access control list simplifies the fashion that users are identified. ACLs ensure that only canonical users and traffic take access to a system.
- Operation. ACLs provide performance advantages over other technologies that perform the aforementioned role. They are configured directly on the routing device's forwarding hardware, so access control lists do not have a negative operation effect on routing devices. Compare this to a stateful inspection firewall, which is a separate slice of software that may cause performance degradation. Also, controlling network traffic enables networks to be more efficient.
- Control. ACLs can give administrators more granular control over user and traffic permissions on a network at many different points in the network. They help control admission to network endpoints and traffic flowing between internal networks.
Where can you place an access command listing?
Access control lists can be placed on virtually any security or routing device, and having multiple ACLs in unlike parts of the network tin can be beneficial.
ACLs are well suited to network endpoints -- similar applications or servers -- that require high speed and performance, too as security.
Network administrators may choose to place an admission control list at different points in the network depending on the network architecture. ACLs are oft placed on the edge routers of a network considering they border the public internet. This gives the ACL a take a chance to filter traffic earlier it reaches the rest of the network.
Border routers with ACLs tin be placed in the demilitarized zone (DMZ) between the public internet and the balance of the network. A DMZ is a buffer zone with an outward-facing router that provides full general security from all external networks. It also features an internal router that separates the DMZ from the protected network.
DMZs may comprise dissimilar network resources, like application servers, web servers, domain proper name servers or virtual individual networks. The configuration of the ACL on the routing device is different, depending on the devices behind it and the categories of user that demand access to those devices.
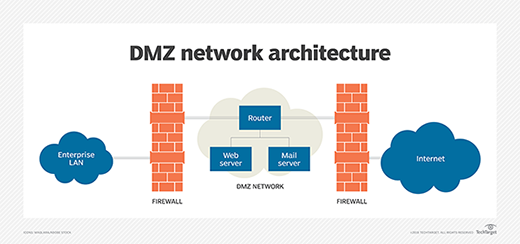
Components of an admission control list
ACL entries consist of several different components that specify how the ACL treats different traffic types. Some examples of common ACL components include the post-obit:
- Sequence number. The sequence number shows the identity of the object in the ACL entry.
- ACL proper name. This identifies an ACL using a name instead of a number. Some ACLs permit both numbers and letters.
- Comments. Some ACLs enable users to add comments, which are extra descriptions of the ACL entry.
- Network protocol. This enables admins to allow or deny traffic based on a network protocol, such as IP, Internet Command Message Protocol, TCP, User Datagram Protocol or NetBIOS, for example.
- Source and destination. This defines a specific IP accost to block or allow or an address range based on Classless Inter-Domain Routing.
- Log. Some ACL devices go on a log of objects that the ACL recognizes.
More than advanced ACL entries can specify traffic based on sure IP parcel header fields, like Differentiated Services Lawmaking Indicate, Type of Service or IP precedence.
How to implement an ACL
To implement an ACL, network administrators must understand the types of traffic that flow in and out of the network, equally well as the types of resource they are trying to protect. Administrators should hierarchically organize and manage IT avails in separate categories and administer different privileges to users.
A standard ACL listing is generally implemented shut to the destination that it is trying to protect. Extended access control lists are generally implemented close to the source. Extended ACLs can be configured using admission list names instead of access list numbers.
The basic syntax used to create a standard numbered admission control list on a Cisco router is as follows:
Router (config)# access-listing (1300-1999) (allow | deny) source-addr (source-wildcard) The diverse parts mean the post-obit:
- (1300-1999) specifies the ACL IP number range. This names the ACL and defines the type of ACL. 1300-1999 makes this a standard ACL.
- (permit | deny) specifies the packet to permit or refuse.
- Source-addr specifies the source IP address.
- Source-wildcard specifies the wildcard mask.
A wildcard mask tells a router which bits of an IP accost are available for a network device to examine and determine if it matches the access list.
Users can enter the above configuration lawmaking into the control line to create the access control list. Cloud platforms from vendors, including Oracle and IBM, likewise typically offer an option to create an access control list in their user login portal.
Setting user permissions throughout a computer system tin be tedious, but in that location are ways to automate the script .
Access control lists must be configured differently based on differences in network architecture. This includes differences betwixt on-premises, physical networks and cloud networks. Learn the basics of cloud network compages and network management.
​what Type Of Access Control List Defines The Settings For Auditing Access To An Object?,
Source: https://www.techtarget.com/searchnetworking/definition/access-control-list-ACL
Posted by: brocksualk1945.blogspot.com


0 Response to "​what Type Of Access Control List Defines The Settings For Auditing Access To An Object?"
Post a Comment